Welcome to our Blog
At iPing, we are committed to keeping our clients and readers informed about the ever-evolving landscape of technology and how it impacts businesses. Through our blog posts and news articles, we provide expert analysis, practical tips, and thought-provoking content that can help you stay ahead of the curve and make informed decisions for your IT strategy.
- iPing
Are you a business owner looking for new ways to increase efficiency and capitalize on growth opportunities? Outsourcing your IT support is an effective solution that can help bring more stability to your operations while also freeing up resources to focus on core objectives. In this blog post, we will explore the benefits of outsourcing your IT support to a reliable provider so that you can make the best decision for your business.
Why your business should consider outsourcing IT support - what are the benefits of outsourcing your IT Support?
Outsourcing IT support has become increasingly popular among businesses of all sizes in recent years in Ireland. Outsourcing IT support can bring tremendous benefits to your business.
- Firstly, it allows you to tap into a pool of technical experts who have extensive knowledge and experience in their field. This means you can access the latest and most innovative technologies, which can improve the efficiency and effectiveness of your operations.
- Additionally, outsourcing IT support can be a cost-effective solution as you do not have to invest in hiring and training a full-time in-house IT team. Instead, you can focus on your core business activities knowing that your IT needs are being managed by professionals.
- Outsourcing IT support is a smart choice for businesses looking to enhance their technological capabilities and streamline their operations, get expert advice and support and the benefit of significant cost savings.
Outsourcing allows a business to focus on its core competencies, rather than spending valuable time on IT issues.
Identifying potential partners for outsourced IT support
Finding the right partner for outsourced IT support can be a daunting task. With so many options available, it can be difficult to identify the right fit for your business. However, taking the time to research potential partners and their services can yield significant benefits in terms of cost savings, improved technology infrastructure, and access to expert knowledge.
Do not settle for just any IT support provider - choose a partner that understands with your business needs and goals, and that can provide a reliable and responsive service.
Steps to ensure successful IT outsourcing
Outsourcing your IT solutions can be a successful move for your business, but it is essential to take certain steps to ensure that the process goes smoothly.
- First, take the time to research potential providers carefully and choose one that aligns with your business's objectives.
- Set clear expectations and communication channels upfront, with specific deliverables and deadlines specified in writing.
- Additionally, make sure to have a solid plan in place for monitoring and evaluating the outsourcing relationship's progress.
- Finally, be proactive in addressing any issues or concerns that arise - don't let problems fester and potentially damage the partnership.
By following these steps, outsourcing your IT solutions can be an effective way to streamline your business operations and free up resources for other business priorities.
Potential pitfalls when outsourcing IT support
Outsourcing your IT support can be a wise decision, but it is important to be aware of potential pitfalls. One common mistake is choosing the wrong provider, leading to missed targets and slow response times. Additionally, communication barriers can arise when working with a team in a different time zone or cultural context, causing frustration and misunderstandings. Finally, security risks must be carefully managed to protect sensitive data. By taking the time to find the right provider, communicate effectively, and implement strong security measures, you can avoid these pitfalls and enjoy the benefits of outsourcing IT support.
Strategies to maximize ROI from outsourced IT support
When it comes to getting the most out of your outsourced IT support, a few key strategies can make a significant difference.
- First, clearly define your objectives and expectations and communicate them clearly to your provider. This will help ensure everyone is on the same page and working towards the same goals.
- Next, make sure to establish clear lines of communication so you can quickly and easily address any issues that may arise. Regular check-ins and status updates can help keep everyone on track and prevent small problems from turning into big ones.
- Finally, do not be afraid to ask questions or request additional support as needed. Your IT provider should be a true partner in your business success and maximizing your ROI means making the most of that partnership.
iPing are an Irish based Outsource IT support for small and medium sized businesses. We help business grow by ensuring their IT systems are operating fully at all times and if there are IT issues, we are on it straight away.
We provide back Up, technical updates, monitoring, IT strategic advice, protection, but most importantly we keep your IT systems operating so you can focus on your business.
See here for more information on our Outsourced IT Support service.
- iPing
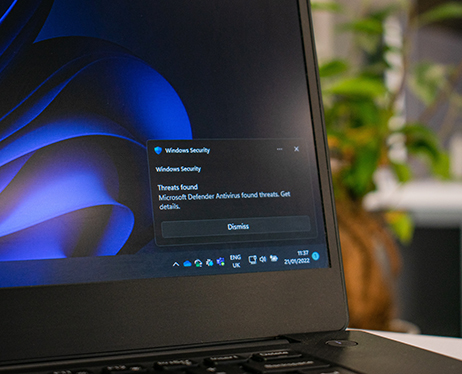
As technology advances and more of our lives move online, cyber security breaches have become more common. Unfortunately, this has increased the risk of businesses, organisations and individuals suffering from financial loss and a damaged reputation.
In this blog post we will explore the causes of cyber security breaches as well as the impacts they can have. We will also discuss some strategies that can be employed to help prevent such breaches from happening in the first place.
Causes of Cyber Security Breaches
The primary cause of cyber security breaches is human error.
- People may unknowingly click malicious links or open emails from untrustworthy sources, allowing hackers access to their data.
- Malware attacks are another source of cybersecurity problems, with hackers creating viruses designed to exploit weak points within systems or networks.
- Unauthorised access by third-party actors is yet another means through which criminals can gain access to valuable data or information.
- Poor system maintenance and lack of sufficient protection leave systems vulnerable to attacks even if there are no malicious actors involved.
Impact of Cyber Security Breaches
The impact of cybersecurity breaches can be severe for both businesses and individuals alike.
- From a business perspective the primary risks include financial losses due to stolen funds or theft of confidential data such as customer records or trade secrets.
- There is also reputational damage resulting from negative publicity or legal action against the company responsible for the breach in question.
- From an individual’s point-of-view personal information such as bank details, credit cards numbers and other sensitive information may be exposed making them vulnerable to identity theft or fraud.
There have been several high-profile cyber security breaches in recent years that have affected millions of people worldwide. Here are some examples:
SolarWinds hack: In December 2020, it was discovered that a group of hackers had infiltrated SolarWinds, a software company that provides IT management solutions to various organisations. The hackers inserted malware into SolarWinds’ software updates, which then spread to the company’s customers, including several US government agencies. It is believed that Russian state-sponsored hackers were behind the attack.
Colonial Pipeline ransomware attack: In May 2021, Colonial Pipeline, one of the largest fuel pipeline operators in the US, was hit by a ransomware attack. The hackers demanded a ransom in exchange for the release of the company’s computer systems, which caused a major disruption to the fuel supply chain on the East Coast of the US.
JBS ransomware attack: In June 2021, JBS, one of the world’s largest meat processing companies, suffered a ransomware attack that led to the shutdown of its operations in several countries, including the US, Australia, and Canada. The hackers demanded a ransom to unlock JBS’ systems and data.
Microsoft Exchange Server hack: In March 2021, it was discovered that a group of Chinese state-sponsored hackers had exploited a vulnerability in Microsoft Exchange Server, an email and calendar software used by many organisations, to gain access to sensitive information. The hack affected tens of thousands of organisations worldwide.
Equifax data breach: In 2017, Equifax, a US-based credit reporting agency, suffered a data breach that exposed the personal information of over 143 million people. The breach was caused by a vulnerability in the company’s web application framework and resulted in one of the largest data breaches in history.
These examples demonstrate the importance of strong cyber security measures and the need for organisations to remain vigilant in the face of increasing cyber threats.
Prevention Strategies for Cybersecurity Breaches
Fortunately, there are measures that can be taken to reduce the chances that these kinds of incidents occur in future.
- For businesses it is important to establish clear policies around cyber security through employee training programs so that staff members have adequate knowledge on how best to protect their systems from attack.
- Strict control protocols should also be enforced including passwords protocols, authorization procedures and encryption standards where applicable.
- Additionally, companies should consider implementing additional layers of network protection such as malware scanners and firewalls to help detect unauthorised access attempts before they become successful attacks.
For individuals, education is key when it comes to avoiding cyber security breaches in future; customers need to be made aware of threats posed by cyber-crime so that they understand how best to stay safe when working online or engaging with digital services for example banking apps or shopping websites etc.
By following these strategies companies should be able reduce the chances that their services are targeted by criminals in future while helping ensure that customers remain safe online too.
These are issues that iPing can assist with, we appreciate that our customers are busy and that they don’t always have the time to be completely diligent with IT security issues. Why not let iPing take of these worries for you and provide you with complete IT peace of mind?
- iPing
It’s no secret that email is one of the world’s most widely used forms of communication. What may be less well-known, however, is the fact that email is also one of the most vulnerable forms of communication. Email security is essential for protecting email communications from unauthorized access or interception. Encryption, password protection, and authentication are all measures that can be taken to improve email security.
What is email security, and why is it important?
Email security is the process of protecting email communications from unauthorized access or interception. Email is a widely used form of communication and is therefore vulnerable to attacks. Email security measures can include encryption, password protection, and authentication.
There are several reasons why email security is essential. First, email is a valuable communication tool that can send sensitive information, such as passwords or credit card numbers. If this information falls into the wrong hands, it could be used for identity theft or other malicious activities.
Second, email is often not secure by default, and messages can be easily intercepted or read if they are not encrypted. And third, email is a popular target for hackers. Hackers can use email to launch spam or phishing attacks or to gain access to confidential information.
Email security is essential for protecting email communications from unauthorized access or interception. Encryption, password protection, and authentication are all measures that can be taken to improve email security. By accepting these precautions, businesses can help protect their confidential data and ensure that their email communications are safe and secure.
How can email be encrypted to improve security?
Encryption is transforming readable data into an unreadable format, which can be done using a password or key. An email is encrypted and converted into an unreadable format that can only be decrypted with the correct password or key.
Encryption is a valuable tool for improving email security. It can help protect email communications from unauthorized access or interception. In addition, encryption can help ensure that the privacy of email messages is maintained. By encrypting email messages, businesses can help protect their confidential data and keep their email communications safe and secure.
What are some measures that can be taken to protect email passwords?
Passwords are a vital component of email security and help protect email communications from unauthorized access or interception. There are several measures businesses can take to ensure the safety of email passwords.
First, businesses should use strong passwords, and a strong password is difficult to guess and is not easily cracked. A strong password should also be extended and include a mix of letters, numbers, and symbols.
Second, businesses should never use the same password for multiple accounts. If a hacker obtains your email password, they will also have access to your other accounts.
Third, businesses should store their passwords in a safe place. This could mean keeping them in a locked drawer or using a password manager software program.
Fourth, businesses should regularly change their passwords. Companies can help protect themselves from hackers who may have obtained old passwords by periodically evolving them.
By taking these measures, businesses can help protect their email passwords and keep their email communications safe and secure.
How can email authentication be used to improve security?
Authentication is the process of verifying the identity of a person or entity. Email authentication is the process of verifying the identity of the sender of an email message. This can be done using a password or key.
Email authentication is a valuable tool for improving email security. It can help protect email communications from unauthorized access or interception. In addition, email authentication can help ensure that email messages are not spoofed or forged. By authenticating email messages, businesses can help protect their confidential data and keep their email communications safe and secure.
There are several email authentication methods that businesses can use. These include Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC). By using these authentication methods, businesses can help improve email security and protect their email communications.
Email security is important for businesses of all sizes. By taking measures to improve email security, businesses can help protect their confidential data and ensure that their email communications are safe and secure.
Wrap-up
Email security is the process of protecting email communications from unauthorized access or interception. Email security measures can include encryption, password protection, and authentication. By taking these precautions, businesses can help protect their confidential data and ensure that their email communications are safe and secure.
- iPing
It is no secret that we live in a world dominated by technology. The average person relies on their computer, phone, or other electronic devices for just about everything. From shopping to banking to communicating with loved ones, our lives are intertwined with technology in ways that were once unimaginable. It is more important than ever to protect our devices from viruses, malware, and other online threats.
While there are several ways to do this, one of the most effective is installing and using anti-virus software. Anti-virus software is designed to detect and remove malicious software from your devices, keeping them safe from harm.
The importance of anti-virus software
In today’s digital age, our lives increasingly rely on computers and mobile devices. We use them for everything from communication and entertainment to work and banking. However, as we store more and more personal information online, we become more vulnerable to cybercrime. One way to protect ourselves from these threats is to use anti-virus software.
Anti-virus software works by scanning your computer for malicious files and quarantining or deleting them. This can help to prevent viruses, malware, and other online threats from causing harm to your computer. In addition, anti-virus software can also help to protect your privacy by blocking unwanted tracking cookies and ads. As we become increasingly reliant on technology, we must take steps to protect ourselves online. Anti-virus software is one of the best ways to do this.
The different types of anti-virus software available
Anti-virus software is a crucial piece of protection for any computer. Many kinds of anti-virus software are available, each with its own strengths and weaknesses. Some popular anti-virus programs include BitDefender, Symantec, ESET, and Avast.
Each of these programs offers a different level of protection, so choosing the one that best meets your needs is essential. For example, ESET is known for its comprehensive protection against viruses, while Symantec is good at detecting and removing spyware. On the other hand, Avast is a decent all-around choice that offers adequate protection against viruses and spyware.
How to choose the right anti-virus software for your needs
In the market for anti-virus software? With so many options available, it can be tough to know where to start. The first step is to assess your needs. Are you looking for basic protection against malware, or do you need something more robust to handle tasks like data encryption and password management? Once you have a good idea of your needs, you can start narrowing down your choices.
Next, take a look at the different features each option offers. Some anti-virus software is better at detecting and removing malware, while others focus on preventing infections in the first place. And while most programs provide basic protection against common threats, some include extras like parental controls or online backup. Consider which features are most important to you, and then compare prices to find the best value. With a bit of research, you should be able to find the perfect anti-virus software for your needs.
The benefits of using anti-virus software
In the internet age, protecting your computer from viruses is more important than ever. Virus protection software helps to block harmful programs from infecting your system, and it can also remove any viruses that have already infiltrated your computer. While no software can guarantee 100% protection, using an anti-virus program is one of the best ways to reduce your risk of infection.
In addition to protecting your computer, anti-virus software can also help to protect your personal information. By preventing hackers from accessing your system, you can help to keep your financial and medical information safe from identity theft. In today’s digital world, investing in anti-virus protection is essential for anyone who wants to safeguard their computer and their personal information.
The cost of anti-virus software
When protecting your computer from viruses, there is no such thing as being too safe. That’s why it’s crucial to invest in quality anti-virus software. However, the cost of these programs can vary widely, making it difficult to know how much to budget for this necessary expense. Home users can generally expect to pay anywhere from €50 to €100 per year for a good anti-virus program. For businesses, the cost could be significantly higher, depending on the number of devices that need protection.
Of course, the price is not the only factor to consider when choosing an anti-virus program. It’s also important to research different programs to find one that will work well with your existing system and meet your specific needs. With so many options on the market, there is no excuse for not being adequately protected against viruses.
How to install and use anti-virus software
Installing anti-virus software is a critical first step in protecting your computer from malware. But simply installing anti-virus software is not enough – you also need to keep it up-to-date and ensure it is running correctly. Here are some tips on how to do just that.
First, download the latest version of your chosen anti-virus software. Then, follow the instructions for installing it on your computer. Once it is installed, run regular scans of your system – at least once a week, but more often if possible. If you suspect your computer has been infected with malware, run a scan immediately.
Most anti-virus software will also allow you to schedule regular scans, which can help ensure that you don’t forget to scan your system regularly. Finally, keep your anti-virus software up-to-date by downloading and installing the latest updates as they become available. By taking these simple steps, you can help protect your computer from malware.
Wrapping Up
Anti-virus software is essential for anyone who wants to protect their computer from harmful viruses. While the cost of these programs can vary, they are an important investment in the safety of your system. In addition to preventing infection, anti-virus software can also help to protect your personal information from identity theft. Following the simple steps outlined in this article can help keep your computer safe from harm.
- iPing
The ability to continue critical operations during an unplanned disruption is vital for modern businesses. These unplanned disruptions can stem from adverse weather events, severe cybersecurity incidents, third-party vendor outages, and human error. You can’t control unexpected events, but you can control how you respond to them. This article highlights six best practices for business continuity at your business.
The Costs of Business Continuity Events
The prospect of an outage that threatens the ability to continue running essential business operations is a daunting one. Gartner estimates the cost at $5,600 (€4,750) per minute of IT downtime. This figure varies across sectors, but there is no doubt that a business continuity event has the potential to inflict enormous costs.
A large proportion of the significant costs of a business continuity event come from the loss of revenue, lost customers, and reduced employee productivity. Consider an eCommerce business selling products from their website—each minute the website isn’t available to potential customers means you can’t sell your products and those prospects will find another business to buy from. Businesses that suffer an extended disruption are likely to suffer further reputational damage in today’s demanding customer environment. Business Continuity Best Practices
Here are six best practices for business continuity.
1. Make A Plan
Having a solid business continuity plan is the key enabler of resilience in responding to unexpected disruptions to business services. Without a documented plan, your response is likely to be uncoordinated and chaotic. Not having a plan in place makes swiftly recovering important business services is extremely unlikely, which worsens the costs inflicted by unexpected disruptions.
A business continuity plan establishes clarity about the processes for responding to adverse events, the roles of different employees in responding, and the communication protocols if primary communication mediums are taken offline.
It’s important to get strategic buy-in for business continuity plans from the top down if your plan is going to have any impact. Make sure you consider your specific industry when drawing up a plan to ensure everyone is on board with it. For example, if you’re a small online business with a mostly remote workforce using cloud infrastructure, you probably don’t need to be planning for the impact of a flood.
2. Know Your Vulnerabilities
A crucial part of business continuity is to have a complete picture of the key risks and vulnerabilities your business faces. The objective is to understand what processes and assets are critical to business operations and in what ways are they at risk. Every business has limitations in budget and personnel, which means that it’s not practical or sensible to address every possible adverse event or risk to every business process.
Hone in on the key systems that support your business and list all the ways they are at risk of disruption. Knowledge of these vulnerabilities provides the foundation for putting in place appropriate response strategies that can get these business systems online and protect important business assets as quickly as possible.
3. Choose Recovery Strategies
It’s essential to carefully choose and plan your recovery strategies as a business continuity best practice. Documenting the business and technology responses is the number one way to prevent a panicked response in which your business scrambles to identify what systems to prioritize and how to recover them after an unplanned disruption. Furthermore, analyzing the available recovery options helps you choose the most practical options in the face of previously identified vulnerabilities and constraints on the available budget.
The following are some points to think about when opting for recovery strategies:
- Communication redundancy—it’s wise never to rely on one communication method. If your team primarily communicates by email, make sure to have at least one more communication method that doesn’t depend on a functioning email system.
- Limit single points of failure—when choosing recovery options, such as data backups, don’t rely on a single vendor.
- Adequate environmental safeguards—even in a remote world, most businesses retain some sort of centralized office presence. It’s important to put in place adequate safeguards against various hazards at your physical business location, including fire extinguishers, smoke alarms, and even anti-flood defenses if that’s a risk in your area.
4. Use Automation
The human component of business continuity can’t be neglected, however, the best business continuity plans incorporate automation throughout. Automation enables agility and efficiency, both of which help to rapidly restore affected business operations in the aftermath of a flood, fire, cyber attack, or any other unexpected event that takes systems offline.
This automation should be software-driven, with disaster recovery services handling processes such as backing up data and initiating cloud failover as soon as critical systems or apps become unavailable.
5. Leverage Cloud Infrastructure
Most modern businesses are driven by technology even if they don’t consider themselves technology companies. For example, a small local dental practice depends upon the availability of IT systems to manage patient appointments and records. Given the inextricable intertwining between business processes and IT systems, it makes sense to focus heavily on restoring those IT systems in the event of an outage.
One of the best uses of cloud infrastructure is running cloud-based applications that don’t depend on on-premise systems. You can still access cloud-based applications from a laptop even if your company’s IT systems experience an outage.
Another way to use the cloud is as a failover option to build redundancy into your critical applications and infrastructure. Cloud failover servers can immediately restore and run crucial business applications in the event of an outage so that your most valuable business operations are minimally impacted by a business continuity event.
6. Test and Update Your Plan
It’s a mistake to think that once you have a documented business continuity plan, you can assume it will remain functional over the lifetime of your company. The right approach is to treat a business continuity plan as a living, constantly evolving document that you update in line with your evolving business dynamics.
Taking a recent pertinent example, many companies experienced a radical shift to a mostly remote workforce during the Covid pandemic. Any business continuity plan in place before that pandemic would need to be updated to reflect this altered dynamic. To ensure business continuity in this landscape, companies would’ve needed to put in place solutions that ensured high availability and failover for remote access services, such as VPNs or cloud-based applications.
A regular testing program ensures that the recovery solutions and workflows you have in place actually work. There’s nothing worse than experiencing a genuine outage only to find that there’s a problem that prevents the resumption of key business operations. The prevailing wisdom is to conduct a high-level test at least twice per year to identify any gaps in your business continuity plan.
Wrapping Up
Successful business continuity requires a strategic approach and a mindset shift that prioritizes business continuity as central to ongoing business operations rather than as a form of insurance against unlikely events. The global pandemic taught businesses in all industries that these unlikely events shouldn’t be an afterthought. Unplanned events are always a risk, and being prepared can pay dividends.
If you need help implementing a business continuity strategy at your business, contact iPing today.
- iPing
The impending release of Microsoft Windows 11 in 2021 poses a dilemma for businesses about whether they should upgrade to this new version of the operating system. The key consideration with any decision for undertaking an IT upgrade project is whether it’s worth the effort. This article highlights some of the benefits and drawbacks for businesses considering an upgrade to Windows 11.
Windows 11 Upgrade Benefits
Windows is a hugely popular operating system favoured by most businesses because users are very familiar with Windows. The popularity of Windows 10 has reached the point that by October 2020, this version of Windows accounted for 72.2 per cent of Windows-only machines
It’s worth noting that Windows 11 is a free upgrade, so there aren’t any direct monetary costs to consider for the actual operating system upgrade. But the decision to upgrade is more nuanced than that, and indirect costs can often emerge for free upgrades. Here are some specific benefits to businesses of Windows 11.
Better Teams Integration
Windows 11 appears to be built with a remote workforce in mind. Teams integration has been extended to the taskbar so that it’s possible to instantly connect with coworkers via text, chat, voice, or video. You can also share your screen with the click of a button.
Even if the party you’re communicating with from Teams doesn’t have the Teams app installed, you can SMS each other from your Teams app. This heightened Teams integration appears to be a direct response to the Covid pandemic and how it shaped the workforce.
Streamlined User Interface
In a world of declining attention spans and endless notifications, it’s good to see Microsoft developers make an effort to declutter and streamline the user interface. Windows 11’s interface design comes with subtler animations, softer sounds, rounded corners, and less clutter to reduce the cognitive load of interacting with the desktop.
Snap Layouts and Snap Groups provide new ways for users to optimize screen real estate and view apps side by side. The emphasis here is to help your employees stay more productive throughout the day by focusing on the tasks they need to do, which is obviously a plus from a business standpoint.
Built for Hybrid IT Environments
Related to the previous point, Windows 11 will provide great support for hybrid IT environments. Many businesses use a mix of on-premise applications and apps hosted in the cloud. The hybrid IT environment is a huge influence in making remote work possible.
Windows 11 interacts with cloud platforms and apps through a front-end interface rather than via a web browser. The result is that users interact with cloud-based applications the same way as they would when interacting with an app hosted locally on the network.
Security Focused
Recognizing the serious cyber threat landscape in which every business operates, Microsoft is pushing Windows 11 as a zero-trust operating system. These security features require the mandatory inclusion and switching on of Trusted Platform Module (TPM) 2.0 chips. TPM chips can protect and encrypt data and operate in quarantine mode in the event of a security compromise.
The concept of zero trust is to never trust and always verify. In practice, this means that the TPM chips will use biometrics information to authenticate users when they log in. Mandatory virtualization-based security (VBS) isolates a secure memory region for added vulnerability protection. These features are all positives because hardening endpoints is a great way to protect against common cyber threats like malware, ransomware, and trojans.
Annual Updates
The semi-annual feature updates that often require lengthy levels of system downtime are now becoming annual updates with Windows 11. Each annual update will release in the second half of every calendar year. Enterprise editions of Windows 11 get 36 months of support from the release date of each update, which is an improvement of 6 months over Windows 10.
Windows 11 Upgrade Drawbacks
The announcement of Windows 11 came as somewhat of a surprise. Back in 2015, a Microsoft executive said nobody was working on Windows 11. Most industry analysts expected Windows 10 to continue rolling on with regular security updates as needed and the infrequent addition of new features. So, are there any drawbacks?
While the benefits sound good on paper, it’s not at all obvious whether these benefits will come to fruition. Nor will any of the benefits prove particularly revolutionary for employee workloads. For example, Microsoft’s marketing of Windows 11 as the most secure operating system to date has been heard before for previous Windows versions. But pretty much anyone who has ever used a previous Windows version has experienced the slew of security patches required on a monthly basis to fix security vulnerabilities in the operating system.
An even bigger drawback, however, is that your company’s desktop workstations may not even be able to run Windows 11. In order to achieve the proposed zero-trust security features, Windows 11 has a requirement for TPM 2.0 chips that must be switched on.
These need to be built into the system on which the OS runs. If your desktop workstations are older than 5 years, they’re unlikely to support Windows 11 without separately buying and installing the TPM chips. This is a huge drawback because it means a Windows 11 upgrade requires significant hardware investments that your company may not afford right now.
There are also additional hardware requirements to meet, including 1GHz or faster dual-core processors, 4GB of RAM, and 64GB of storage. It’s also worth pointing out that Microsoft will provide Windows 10 updates until October 2025, so the decision to upgrade doesn’t have to be a hasty one. Take your time and seek the best advice for your company’s needs.
Closing Thoughts
Whether it’s worth upgrading to Windows 11 or not depends on your particular business and your existing IT infrastructure. To make the most informed decision about an upgrade, you can seek expert advice from the iPing team. We’ll listen to your requirements and advise on the feasibility and necessity of a Windows 11 upgrade. Contact us today.
- iPing
Ransomware attacks target organizations around the world all the time. Irish businesses of all sizes became aware of the threat of ransomware when the HSE disclosed the devastating cyber attack on its IT infrastructure in May 2021. This post overviews what ransomware actually is and highlights five key strategies for ransomware prevention.
What is Ransomware?
Ransomware is malicious software that blocks access to devices or the data on them by encrypting files. The attackers demand that their victims pay a ransom if they want to remove the encryption and access their files again. Typically, victims find a note displayed on-screen informing them that their files are encrypted along with payment instructions for removing the encryption.
Ransomware is the most widely used method of attack for cybercriminals because it’s potentially incredibly lucrative. As evidence of how lucrative successful ransomware attacks can be, the Colonial Pipeline Company in the United States paid a $4.4 million ransom in May 2021.
Industry predictions state that ransomware attacks will target businesses every 11 seconds by the end of 2021.
Ransomware Prevention Best Practices
The ransoms demanded by hackers typically reach hundreds of thousands of Euros or even millions for SMBs. And even if you pay the hefty ransom, there’s no guarantee you’ll get all your files back. So, when it comes to these attacks, prevention is definitely better than cure.
1. Require Multifactor Authentication
Ransomware attacks often start with social engineering techniques that persuade people to reveal their login credentials to a business application or system. Once the attacker has access to a network using those credentials, they can move through the network and install malicious software that encrypts important files.
A good way to harden your network against this type of entry route is to require multifactor authentication to verify user identities. When you only require a simple set of username-password credentials to verify users and let them log in, all it takes is a persuasive phishing email to expose your entire network. This risky dependence on passwords alone is amplified in a world where employees work remotely and often access resources from their laptops using Remote Desktop Protocol connections.
Multifactor authentication (MFA) requires users to provide an extra type of evidence along with their username-password combination before they can access a system or resource. A username-password pair counts as something users know. The point of MFA is to use another category of evidence to mitigate the risk of password theft.
A good alternative type of evidence to require is something the user has, such as a USB security token that generates one-time PIN codes. Another type of category favoured by some companies is something the user is, which typically means using biometric data like a fingerprint or facial recognition scan.
2. Have a Backup and Disaster Recovery Plan
A big pain point of successful ransomware attacks is not having access to important files, systems, or servers. A solid backup and disaster recovery plan can prevent these issues from arising.
With a recent backup in place, even if someone manages to encrypt the data with ransomware, you can restore it without needing to pay the ransom. A disaster recovery plan can implement failover solutions so that operational disruption is minimal. For example, if key business services or applications get taken down due to a server being encrypted, your disaster recovery plan can kick in and you can resume those services using cloud infrastructure.
The use of backups has been so successful that some cybercrime groups have evolved their ransomware to use a technique known as double-extortion. The use of double-extortion ransomware doesn’t just lock your important data. This type of ransomware also extracts data from your network with a threat to leak it online or sell it.
There is debate within the information security world on whether backup and disaster recovery are still useful tools for ransomware defence. Not all ransomware attacks use double extortion, though, so backing up data remains a valid form of proactive defence against these attacks.
3. Invest in Cybersecurity Awareness Training
Your company’s ability to prevent ransomware is strongly correlated with the level of overall cybersecurity awareness among employees. Cybercriminals know that humans are often the weak link that they can exploit to access your network and encrypt your files.
Cybersecurity awareness training can highlight the common methods outsiders use to gain unauthorized access to business assets. Employees should know about the dangers of opening email attachments or clicking links from untrusted sources. Good training can teach employees how to differentiate between genuine emails versus phishing emails.
The topics worth covering in training include:
- Selecting strong passwords that aren’t easy to guess
- Social engineering techniques and how to protect against them
- The risks of revealing sensitive information on social media
- The importance and use of antivirus, anti-malware, firewalls, and other security solutions
- How to use Wi-Fi networks securely
- How to securely browse the Internet without compromising the business network
Not every business has the capacity to develop its own cybersecurity awareness training modules. There are third-party companies that specialise in this area. Investing in training can definitely pay off in a big way in terms of ransomware prevention.
4. Restrict Privileged Access
Whether you’re managing remote user accounts or any other account on your network, it’s important to restrict privileged access for your users. When an employee has more privileges on the network than they need to perform their daily work, you introduce greater risks should that employee’s account become compromised.
Privileged access can enable hackers to wreak havoc across an entire network. Privileged users can install malicious software on all devices or modify operating system registry keys.
Restricting privileged access puts a limit on the damage that malicious intruders can cause. While some ransomware families can cause damage regardless of privilege level, minimizing privileged access is a good practice that improves your information security and is relatively easy to implement.
5. Use Patch Management
Exploiting users isn’t the only way people can break into a network and install ransomware. Hackers often seek to exploit businesses that run unpatched software, device firmware, and operating systems on their IT infrastructure.
There are various tools that can automate patch management for you. Aside from software and operating systems, you should push patches to WiFi access points, routers, firewalls, intrusion detection systems servers, workstations, and printers when they are released.
Proper patch management keeps all relevant IT services current by applying the latest updates in a timely manner. These updates often address security vulnerabilities that are found and reported to the company that coded the software or manufactured the device. It should be part of your company’s security policy that remote users also apply patches on time for devices they use to connect to your network.
Closing Thoughts
Preventing ransomware is both important and feasible for businesses of all sizes. It’s not an inevitability that your company will become a victim, especially if you adhere to these best practices.
At iPing, we can help Irish businesses prevent ransomware. We provide managed IT services that can spot problems and potential ransomware attack vectors before you even know about them. We also have business continuity services and we can help you support remote workers in a productive, safe way. Contact us today to find out more.
- iPing
Among many interesting findings, the 2021 SonicWall cyber threat report featured a section on the biggest data breaches of 2020 in terms of the volume of records leaked. With the ongoing HSE data breach crippling Ireland’s health system, now is the ideal time to increase security awareness by looking at other major global data breaches and their causes. This article takes a look at the top five data breaches in 2020 and provides some actionable insights on what you can learn from them in terms of your organisation’s IT security posture.
Data Breaches in 2020 and Why They Matter
As you’ll see, several of the companies that were victims of the biggest data breaches were huge companies. Therefore, it’s natural to wonder about the applicability of this information to a small or medium-sized business.
It’s important to realise first of all that malicious intruders don’t solely focus their efforts on large businesses. Businesses of all sizes can learn from the causes of these breaches and take reasonable steps to ensure they don’t repeat these failures.
Secondly, and arguably, more importantly, data breaches are extremely costly. You might not have a database of hundreds of million customers, but many smaller businesses can easily grow a database of 5,000-10,000 customers.
Multiplying the per-record cost of a breach of personality identifiable information (PII) at $150 (~€125) by the size of a small customer database, and you have a bill of well over €500,000 to pay, which will sink most businesses. That’s why this information matters.
1. Estee Lauder Breach: 400 Million Records
The American multinational skincare company Estée Lauder became the victim of 2020’s largest data breach when a security researcher revealed he accessed an exposed database belonging to the company. The database contained a large number of user email addresses in plain text format. Also viewable in the database were internal documents, including audit logs and reports.
Luckily for Estée Lauder, the records didn’t contain any customer information. What was striking about this breach was that it was such a basic security flaw that enabled anyone with an Internet connection to access the data. This breach reinforces the importance of basic information security practices, such as encrypting data and requiring passwords to access them.
2. Facebook 267 Million Records
In 2020, consumer tech website Comparitech revealed they partnered with security researcher Bob Diachenko to uncover a database of 267 million records belonging to Facebook users left exposed online. The data included unique Facebook profile IDs, phone numbers, and full names belonging mostly to users in the United States.
Such data is incredibly valuable for cyber hackers who can use it themselves or sell it on to groups who want to conduct large-scale spam or phishing campaigns. The takeaway message here is that no matter the size of your company, you must take a prudent attitude to always protect sensitive data belonging to customers.
3. Microsoft Breach: 250 Million Records
In January 2020, Microsoft revealed they experienced a major data breach that actually took place over the course of December 2019. The breach revolved around an entire database of “support case analytics” featuring logs of conversations between Microsoft support agents and customers. The database was publicly accessible via the Internet.
In a blog post highlighting what happened, Microsoft described how, “a change made to the database’s network security group on December 5, 2019, contained misconfigured security rules that enabled exposure of the data.” This breach serves as a telling reminder of how misconfigurations pose serious information security risks. Some basic steps for avoiding misconfiguration risks include:
- Applying software updates/patches swiftly
- Disabling default accounts
- Use security scanning tools to look for misconfigurations
- Encrypt your data
4. MGM Resorts 142 Million records
Midway through 2020, reports began to circulate online that data belonging to 142 million MGM Resorts hotel guests was listed for sale on the dark web. The dark web is a part of the web that requires specific software to access. A veritable underworld marketplace in stolen data exists on the dark web where cybercriminals list stolen email addresses, credit card details, and more for sale.
The breach occurred when a hacker compromised a cloud server belonging to MGM resorts and accessed the customer data. This incident again raises questions about the efforts companies are taking to properly secure their cloud resources. It’s vital to be as cautious about securing information in the cloud as it is on-premise. Hospitality is a sector particularly vulnerable to cyber attacks because service providers typically collect customer data that is both personal and financial.
5. Pakistan Mobile Subscribers 115 Million Records
In May 2020, personally identifiable information about mobile subscribers in Pakistan surfaced online. Included in the 115 million breach records were full names, home addresses, and mobile phone numbers. The data was eventually listed for sale on the dark web where an anonymous hacker tried to sell this information for 300 bitcoins.
In terms of its cause, this breach was somewhat mysterious because some records stretched back as far as 2013. Industry commentators speculated the breach took place when a hacker gained access to an old backup file or that it was stolen directly from a server. Whatever the cause, this incident shows that companies around the globe are targets for cyber attacks, not just developed nations.
Closing Thoughts
One key thing that stands out from 2020’s biggest data breaches is the sheer diversity of industries in which the affected companies operate. From skincare to software to hotels, it doesn’t matter what the nature of your business is. In an IT-powered world, the risk of a data breach transcends industries and sectors.
Lastly, it can be somewhat disheartening as an SMB to see that large corporations fall victim to these breaches. You may think, “if they can’t stop breaches with their gargantuan budgets, what hope have we got?”
A more optimistic outlook is also a realistic one, though, because your IT infrastructure is not as complex as that of large-scale enterprises. You don’t have to keep track of as many user accounts, network components, or computing resources.
If you put some basic security measures in place, then you’ve already won half the battle in protecting your valuable data. These basic strategies include:
- Backing up data regularly and ensuring data completeness in backups
- Having offline data backups such as tape storage that can’t be accessed via the Internet
- Applying updates regularly to software, operating systems, and network device firmware.
- Always ensuring you authenticate users before they access data.
iPing can help your business implement these data security methods and avoid data breaches with our managed IT services. Contact us today to learn more.
- iPing
The decision on whether to outsource IT services as a start-up is an important one. There are many challenges faced by startups in terms of deciding what processes to take on versus what you should do in-house.
Ultimately, it’s difficult to facilitate growth when your workload becomes unmanageable. And IT is one of those tricky areas in which small problems can compound into big ones that take too much time and resources to fix alone. Here are six reasons start-ups should outsource IT services.
#1. Focus on The Core Business
Start-up founders are ambitious people who attempt to bring unique, innovative products and services that solve problems to a market. As a start-up founder, you want to grow and scale your business to serve a larger share of a market.
In the initial stages of your start-up project, your focus needs to be on the core business as much as possible. Handling IT services and the inevitable problems you’ll encounter can distract you from that core business.
Even if you have one or two co-founders with decent IT knowledge, the time spent on monitoring, configuring, and fixing IT systems and services is time that would be better spent on marketing your key product or service or improving its quality.
#2. Improved Information Security
Startups with limited information security expertise are easy targets for cybercriminals in the early stages of their growth. Some people mistakenly assume cybercriminals only target established enterprises because their data is more lucrative.
However, the statistics show that 43% of cyber attacks target small companies. While start-ups ultimately aim to become established large businesses through aggressive growth, they typically begin their journey as small operations.
You might understand the basics of running an IT department, but IT security is a different challenge. Cybercriminals are sophisticated technology users who can easily bypass basic security controls. Outsourcing your IT services can drastically improve information security.
#3. Cost Savings
When thinking about the cost of outsourcing IT, it’s helpful to consider the opportunity cost of managing your IT services alone. Bearing in mind that start-ups want to focus on aggressive business growth and scale quickly, getting bogged down by disruptions to IT services or system configurations ends up costing you time and money.
When you outsource your IT services, you’re hiring a dedicated team of people to support your business operations and help solve IT problems that you can’t afford to waste time on. For a start-up, time is money.
#4. Disaster Recovery
Many modern start-ups are highly dependant on a functioning IT system to support the delivery of key business services and products. What happens if your systems go offline and you don’t have a way to get them back? Even if you don’t want to outsource the bulk of your IT support or operations, it’s prudent to outsource disaster recovery.
Preparing for and executing a disaster recovery plan is beyond the scope of most small in-house IT teams. You’ll need specialists who help you recover your critical systems swiftly in the aftermath of a significant IT outage.
#5. Make Better Investments
An underrated benefit of partnering with a well-informed managed services provider is that you’ll get solid advice on choosing the most appropriate hardware and software solutions to meet the needs of your business.
Start-ups often assume they need the fanciest hardware or the most complex software and they acquire such investments at a high cost. Managed IT services can provide the advice you need to make the right investment. An MSP can cut through the noise and evaluate existing IT infrastructure to suggest the investments you actually need versus what would be nice to have.
#6. Not Getting Left Behind
Even if you or your co-foudners are adept with current processes, services and tools, IT, like any other aspect of technology, is a fast-paced and dynamic sector. It’s easy to become distracted by your core business idea and goals to the point where you get left behind in terms of the IT systems, tools, and processes that best support your company.
Outsourcing IT services as a start-up can provide an automated way of ensuring you don’t get left behind. Solid managed IT companies will stay on top of the latest trends, developments, and tools that streamline your IT processes. A well-informed managed services provider can give you invaluable advice about the current tools, hardware, and solutions that best suit the needs of your growing startup.
Closing Thoughts
Success as a start-up ultimately depends on achieving sustainable growth. Outsourcing IT services in the initial growth phase provides many benefits that can help support and achieve success for innovative companies, regardless of their industry.
If you are a co-founder at a start-up and you’d like some help with managing your IT services, contact us today to see what we can do to support your growth.