Welcome to our Blog
At iPing, we are committed to keeping our clients and readers informed about the ever-evolving landscape of technology and how it impacts businesses. Through our blog posts and news articles, we provide expert analysis, practical tips, and thought-provoking content that can help you stay ahead of the curve and make informed decisions for your IT strategy.
- iPing
Huawei Fibre To The Room (FTTR): Revolutionising Connectivity for Dublin SMEs
In today’s fast-paced digital world, reliable and high-speed internet is no longer a luxury—it’s a necessity. For small and medium-sized enterprises (SMEs) in Dublin, staying competitive means embracing cutting-edge technology that enhances productivity, supports growth, and future-proofs operations. Enter Huawei Fibre To The Room (FTTR), a revolutionary solution that brings ultra-fast, stable, and scalable connectivity to every corner of your business.
In this blog, we’ll explore how Huawei FTTR can transform your Dublin-based SME, helping you stay ahead in an increasingly connected world.
What is Huawei Fibre To The Room (FTTR)?
Fibre To The Room (FTTR) is the next evolution in fibre optic technology. Unlike traditional broadband or even Fibre To The Home (FTTH), which brings fibre connectivity to a single point in a building, FTTR extends fibre optic cables to every room. This ensures that every device, whether it’s a computer, smartphone, or IoT sensor, benefits from lightning-fast speeds and unparalleled reliability.
Huawei, a global leader in telecommunications, has pioneered this technology, making it accessible and affordable for SMEs. With FTTR, your business can enjoy gigabit internet speeds, minimal latency, and a network that’s ready to handle the demands of tomorrow.
Why Dublin SMEs Need FTTR
Dublin is Ireland’s economic powerhouse, home to a thriving tech scene and a growing number of SMEs. However, with this growth comes increased competition and higher expectations from customers and partners. Slow or unreliable internet can hinder productivity, disrupt operations, and even damage your reputation.
For Dublin-based SMEs, the challenges are clear:
-
Remote Work: With hybrid and remote work models becoming the norm, employees need seamless connectivity to collaborate effectively.
-
Cloud-Based Tools: Many SMEs rely on cloud services for storage, software, and communication. Slow internet can lead to frustrating delays.
-
Customer Expectations: Customers expect fast, efficient service. Whether you’re running an e-commerce site or a consultancy, slow connectivity can drive them away.
Huawei FTTR addresses these challenges head-on, providing a solution that’s not just fast but also reliable and scalable.
Key Benefits of Huawei FTTR for Dublin SMEs
1. Ultra-Fast Internet Speeds
Imagine downloading large files in seconds, streaming high-definition videos without buffering, or hosting seamless video conferences with clients across the globe. With Huawei FTTR, gigabit speeds are a reality. This means faster data transfers, smoother operations, and happier employees.
For example, a Dublin-based design agency could benefit from quicker uploads and downloads of large graphic files, while a financial consultancy could enjoy real-time access to cloud-based analytics tools.
2. Enhanced Reliability and Stability
There’s nothing more frustrating than internet downtime or laggy connections. Huawei FTTR ensures that your business stays online, even during peak usage times. With fibre optic cables running to every room, you’ll experience minimal latency and maximum uptime.
This is particularly important for SMEs that rely on VoIP systems, video conferencing, or online transactions. A stable connection means fewer disruptions and a more professional image.
3. Future-Proofing Your Business
Technology is evolving at breakneck speed, and your business needs to keep up. Huawei FTTR is designed to support emerging technologies like the Internet of Things (IoT), artificial intelligence (AI), and 5G.
For instance, a Dublin retail business could use IoT sensors to monitor inventory in real-time, while a logistics company could leverage AI for route optimisation. With FTTR, your network is ready for whatever the future holds.
4. Improved Productivity and Efficiency
Slow internet doesn’t just waste time—it can also lead to frustration and decreased morale. Huawei FTTR eliminates these issues, enabling your team to work more efficiently.
Whether it’s faster access to cloud-based tools, smoother collaboration between remote teams, or quicker customer service, FTTR can help your business operate at its best.
5. Competitive Advantage
In a city as dynamic as Dublin, staying ahead of the competition is crucial. By investing in Huawei FTTR, you’re not just upgrading your internet—you’re positioning your business as a forward-thinking, tech-savvy leader.
Customers and partners will appreciate the speed and reliability of your services, giving you an edge in a crowded market.
Case Study: FTTR in Action for a Dublin SME
Consider a hypothetical Dublin-based marketing agency with 20 employees. Before switching to Huawei FTTR, the agency struggled with slow internet speeds, especially during peak hours. Video calls would drop, file uploads took forever, and remote employees faced constant connectivity issues.
After installing Huawei FTTR, the agency saw immediate improvements:
-
Video calls became seamless, even with multiple participants.
-
Large design files could be uploaded and downloaded in seconds.
-
Remote employees reported fewer connectivity issues, leading to better collaboration.
As a result, the agency was able to take on more clients, improve customer satisfaction, and boost overall productivity.
Why Choose Huawei for FTTR?
Huawei is a global leader in telecommunications, known for its innovative solutions and commitment to quality. With decades of experience in fibre optic technology, Huawei has designed FTTR to meet the unique needs of SMEs.
Here’s why Dublin businesses trust Huawei:
-
Cutting-Edge Technology: Huawei’s FTTR solution is at the forefront of connectivity innovation.
-
Tailored Solutions: Whether you’re a small startup or a growing enterprise, Huawei can provide a solution that fits your needs.
-
Reliable Support: With a strong local presence, Huawei offers excellent customer service and technical support.
How to Get Started with Huawei FTTR in Dublin
Ready to transform your business with Huawei FTTR? Here’s how to get started:
-
Assess Your Needs: Determine your current and future connectivity requirements.
-
Contact a Provider: Reach out to a local Huawei partner or internet service provider in Dublin.
-
Schedule an Installation: A professional team will install FTTR in your office, ensuring minimal disruption.
-
Enjoy the Benefits: Experience faster speeds, improved reliability, and a future-proof network.
Conclusion
In a city as vibrant and competitive as Dublin, staying connected is key to success. Huawei Fibre To The Room (FTTR) offers a powerful solution for SMEs, delivering ultra-fast, reliable, and scalable internet that can transform your business.
By investing in FTTR, you’re not just upgrading your connectivity—you’re future-proofing your operations, boosting productivity, and gaining a competitive edge. Don’t let slow internet hold your business back. Embrace the power of Huawei FTTR and take your Dublin-based SME to the next level.
FAQ's
1. What is the cost of Huawei FTTR for SMEs?
The cost varies depending on the size of your business and your specific needs. Contact a local provider for a tailored quote.
2. How long does it take to install FTTR in my Dublin office?
Installation typically takes a few hours to a day, depending on the complexity of your setup.
3. Can FTTR work with my existing network infrastructure?
Yes, Huawei FTTR can be integrated with your current network, though some upgrades may be recommended for optimal performance.
4. Is FTTR suitable for small offices or only larger businesses?
FTTR is scalable and can benefit businesses of all sizes, from small startups to large enterprises.
- iPing
In today’s digital-first world, data is the lifeblood of small and medium-sized enterprises (SMEs). Yet, many businesses in Dublin still view IT security as an unnecessary expense rather than a strategic investment. This perception can leave businesses vulnerable in a rapidly evolving threat landscape. IT security is not just about preventing cyberattacks; it’s about safeguarding your business’s future, protecting customer trust, and enabling growth. Here’s why Dublin SMEs need to rethink their approach to IT security.
The True Cost of Cybersecurity Neglect
Neglecting IT security can be catastrophic for Dublin SMEs. Cyberattacks impact not only your finances but also your reputation, which is critical in a tight-knit business community.
| Impact | Example | Cost Estimate |
|---|---|---|
| Financial Losses | Ransomware demands or fraudulent transactions | €50,000 - €100,000 per incident* |
| Reputation Damage | Customers losing trust after a data breach | Long-term revenue decline |
| Legal Penalties | Fines for non-compliance with GDPR | Up to €20 million or 4% of turnover |
*Source: Irish Small and Medium Enterprises Association (ISME)
Consider the case of a Dublin retailer targeted by a phishing scam. While the financial loss was immediate, the long-term damage came from customers questioning the company’s ability to protect their data. Investing in proactive IT security could have prevented such a scenario.
IT Security as a Competitive Advantage
In a city like Dublin, where competition among SMEs is fierce, IT security can be a differentiator. Customers are becoming increasingly aware of the importance of data protection and are more likely to choose businesses that demonstrate a commitment to security.
How IT Security Benefits Dublin SMEs:
-
Building Trust: Irish consumers value businesses that prioritise their privacy and data security.
-
Market Differentiation: Highlighting robust security measures can give you an edge over competitors.
-
Compliance: Staying compliant with GDPR not only avoids fines but also enhances your credibility.
For instance, a Dublin-based e-commerce store that clearly communicates its security policies can attract more customers who prioritise safe transactions. Transparency in security practices can be a winning strategy.
Long-Term Financial Benefits of IT Security Investments
While investing in IT security may feel like a strain on your budget, the long-term savings and benefits are significant. Here’s a comparison:
| Expense Category | Cost Without IT Security | Cost with IT Security |
| Recovery After a Data Breach | €100,000+ | €10,000 - €50,000 (proactive tools) |
| Downtime from Cyberattacks | €10,000 per day | Minimal with preventive measures |
| Training and Employee Awareness | N/A | €5,000 - €10,000 annually |
For Dublin SMEs, these numbers are compelling. Proactive investments in firewalls, antivirus software, and employee training can save both money and peace of mind in the long run.
IT Security Enhances Business Continuity
Dublin SMEs often face not only cyber threats but also operational risks like system failures or human errors. A robust IT security plan ensures your business remains operational even in the face of adversity.
Strategic Integration of IT Security
For Dublin SMEs, IT security should align with your broader business objectives. It’s not just a technical solution but a key enabler of growth and innovation.
Overcoming Common Misconceptions
Many Dublin SMEs hesitate to invest in IT security due to persistent myths. Here’s how to challenge these misconceptions:
-
Myth: IT security is only for large enterprises.
Reality: SMEs are prime targets for cybercriminals due to perceived weaker defences. -
Myth: IT security is too expensive.
Reality: The cost of a breach is far higher than the upfront investment in security tools. -
Myth: IT security slows down operations.
Reality: Modern solutions enhance efficiency while keeping your business safe.
Conclusion
For Dublin SMEs, IT security is no longer optional. It’s a strategic investment that safeguards your operations, builds customer trust, and sets your business up for long-term success. By shifting your perspective from viewing IT security as a cost to recognising it as a growth enabler, you can position your business to thrive in an increasingly digital world.
Call to Action: Assess your current IT security measures today. Get a complimentary IT assessment and consult with Dublin-based cybersecurity experts iPing to craft a tailored strategy for your business.
- iPing
Dublin's business landscape is thriving, with a diverse mix of multinational corporations, innovative startups, and established local enterprises. As the capital city of Ireland and a major European tech hub, Dublin has become a hotbed of economic activity and technological advancement. However, with this growth comes an increasing reliance on technology across all sectors.
In today's digital age, businesses in Dublin face a unique set of challenges when it comes to managing their IT infrastructure. From cybersecurity threats to talent acquisition, the need for robust and comprehensive IT support has never been more critical. This is where professional IT services come into play, offering Dublin businesses the expertise and resources they need to stay competitive in an ever-evolving marketplace.
Comprehensive IT support is no longer a luxury—it's a necessity for Dublin businesses to thrive in today's competitive market. By partnering with a reliable IT support provider, companies can focus on their core competencies while ensuring their technology backbone remains strong, secure, and scalable.
The Unique Challenges Faced by Dublin Businesses
Rapid Growth and Expansion
Dublin's business sector is experiencing unprecedented growth, particularly in the technology, finance, and pharmaceutical industries. This rapid expansion presents several IT-related challenges, including the need to scale infrastructure to meet increasing demands, integrating new technologies seamlessly, and maintaining system performance during periods of growth. Additionally, ensuring data consistency across expanding operations is crucial for businesses looking to manage this rapid expansion effectively.
Cybersecurity Threats
As Dublin positions itself as a global business centre, it becomes an attractive target for cybercriminals. Businesses face significant threats, such as ransomware attacks that target sensitive customer data, phishing schemes that exploit employees, and DDoS attacks that disrupt online services. Insider threats from disgruntled employees or contractors further complicate the cybersecurity landscape, making it essential for Dublin businesses to adopt robust security measures.
Talent Acquisition and Retention
The booming tech scene in Dublin has created fierce competition for skilled IT professionals, leading to several hurdles in talent acquisition and retention. With a limited pool of experienced IT specialists, businesses often struggle to meet the high salaries demanded by top talent. Additionally, retaining skilled employees in such a competitive job market is challenging, and the continuous need for upskilling due to rapidly evolving technologies adds another layer of complexity.
Economic Climate
Dublin's economic landscape can be volatile, impacting IT budgets and priorities. Fluctuating exchange rates can affect technology purchases, while Brexit uncertainties influence business decisions. Businesses are under pressure to reduce IT costs while maintaining quality, and they must balance the need for innovation with fiscal responsibility.
The Role of Comprehensive IT Support
Proactive IT Management
Comprehensive IT support goes beyond simply fixing problems as they arise. It involves a proactive approach to IT management that offers Dublin businesses significant benefits. Regular system monitoring helps prevent downtime and improve productivity, while scheduled maintenance extends the lifespan of IT infrastructure. Capacity planning ensures smooth scalability for growing businesses, and technology roadmapping aligns IT strategy with business objectives, allowing companies to remain competitive and efficient.
Cybersecurity Protection
Given the growing cyber threats, Dublin businesses require robust security measures. Comprehensive IT support provides advanced firewall and intrusion detection systems, along with regular security audits and vulnerability assessments. Employee cybersecurity training programs are essential to mitigate risks, and incident response and disaster recovery planning ensure that businesses are prepared for any potential breaches.
IT Talent Solutions
To address the IT skills gap in Dublin, comprehensive support offers businesses access to a diverse team of IT specialists. This support includes 24/7 coverage, eliminating the need for in-house night shifts. Continuous training and certification for support staff ensure they remain up-to-date with the latest technologies. Flexible staffing options are available to meet the changing needs of businesses, providing the expertise required without the challenges of recruitment and retention.
Cost-Effective IT Solutions
Outsourcing IT support can lead to significant financial benefits for Dublin businesses. By reducing overhead costs associated with maintaining an in-house IT department and offering predictable monthly expenses through managed service contracts, businesses can better manage their budgets. Economies of scale in purchasing hardware and software licences, coupled with minimised downtime-related losses through proactive maintenance, further enhance the cost-effectiveness of comprehensive IT support.
How iPing Can Help Your Business
iPing’s support system is designed to be highly responsive, comprehensive, and tailored to the specific needs of Dublin-based businesses. By providing continuous, proactive, and strategic IT support, iPing ensures that your business operations run smoothly, allowing you to focus on growth and success.
Helpdesk Support and Proactive Monitoring
One of the cornerstones of iPing’s support system is its help desk availability. Where you can reach iPing’s support team via phone, email, or an online ticketing system, ensuring that help is always just a call or click away.
In addition to reactive support, iPing offers proactive monitoring of your IT infrastructure. Through monitoring systems, potential issues are detected and addressed before they can impact your business. Scheduled maintenance tasks, such as software updates and system performance checks, are carefully planned to minimise disruption to your operations.
|
Support Feature |
Description |
|
Helpdesk Support |
Helpful assistance via phone, email, or online ticketing. |
|
Proactive Monitoring |
Continuous monitoring to prevent issues before they occur. |
|
Scheduled Maintenance |
Regular maintenance tasks scheduled to avoid business disruption. |
Incident Response and On-Site Support
When an IT issue arises, iPing’s support team responds rapidly, diagnosing and resolving the problem as quickly as possible. Depending on the nature of the issue, support can be provided remotely or on-site. For more complex problems, senior engineers or specialised teams are involved to ensure efficient resolution.
For issues that require hands-on intervention, iPing offers local on-site support. Their team of IT specialists based in Dublin is ready to be dispatched to your location, ensuring that critical system failures or emergencies are handled with priority.
|
Support Feature |
Description |
|
Rapid Response |
Quick diagnosis and resolution of IT issues, remotely or on-site. |
|
Escalation Protocols |
Senior engineers or specialised teams are involved in complex problems. |
|
On-Site Support |
Local IT specialists available for hands-on intervention when needed. |
IT Consulting, Training, and Custom SLAs
iPing’s support extends beyond just troubleshooting—it also involves strategic IT consulting to help align your technology with your business goals. Regular reviews and planning sessions are conducted to assess the performance of your IT systems and discuss potential upgrades.
Moreover, iPing provides training for your employees, ensuring they are proficient in using the technology and systems in place. This includes cybersecurity training to prevent user-related incidents. Detailed documentation and user guides are also provided to empower your team to handle common issues independently.
iPing offers customised Service Level Agreements (SLAs) that define the level of support you receive, response times, and other critical service metrics. These SLAs are tailored to meet your specific business needs, ensuring that the support provided is exactly what your business requires.
|
Support Feature |
Description |
|
IT Consulting |
Strategic IT consulting and regular planning sessions to align technology with business goals. |
|
Employee Training |
Training programs and documentation to empower your team. |
|
Custom SLAs |
Tailored service agreements to meet specific business needs and expectations. |
Scalability, Feedback, and Continuous Improvement
As your business grows, iPing’s support services are designed to scale with you. Whether you need more frequent support, additional services, or upgraded infrastructure, iPing can adjust its offerings to match your evolving needs. For larger businesses, a dedicated account manager may be provided to ensure consistent, personalised support.
iPing values client feedback and continuously seeks ways to improve its services. Regular feedback loops ensure that your business's needs are always met, and the support services evolve to keep pace with changing requirements.
|
Support Feature |
Description |
|
Scalability |
Support services that scale with your business growth. |
|
Dedicated Account Manager |
Personalised support for larger businesses through a dedicated account manager. |
|
Feedback and Improvement |
Continuous feedback loops to enhance and evolve support services. |
Conclusion
In conclusion, comprehensive IT support is not just an option—it's a critical necessity for Dublin businesses looking to stay competitive in today's technology-driven market. By partnering with a professional IT support provider, companies in Dublin can overcome the unique challenges they face, from rapid growth and cybersecurity threats to talent shortages and economic uncertainties.
The benefits of comprehensive IT support are clear: proactive management prevents issues before they impact business, robust cybersecurity measures protect valuable data and assets, and access to skilled IT professionals is provided without the hassle of recruitment and retention. Additionally, cost-effective solutions offer enterprise-level support at a fraction of the cost.
Don't let IT challenges hold your Dublin business back. Take the first step towards a more secure, efficient, and competitive future by investing in comprehensive IT support today.
Ready to transform your Dublin business with top-tier IT support? Contact iPing on 01 5241350 for a free IT assessment and discover how we can tailor our comprehensive services to meet your unique needs. Let's work together to keep Dublin at the forefront of technological innovation and business success.
- iPing
Your humble phone number is more valuable than you may think. Here’s how it could fall into the wrong hands – and how you can help keep it out of the reach of fraudsters.
What might be one of the easiest ways to scam someone out of their money – anonymously, of course?
Would it involve stealing their credit card data, perhaps using digital skimming or after hacking into a database of sensitive personal information? While effective, these methods may be resource-intensive and require some technical prowess.
What about stealing payment info via fake websites? This may indeed fit the bill, but spoofing legitimate websites (and email addresses to “spread the word”) may not be for everybody, either. The odds are also high that such ploys will be spotted in time by the security-savvy among us or thwarted by security controls.
Instead, bad actors are turning to highly scalable operations that rely on sophisticated social engineering tactics and costs little to operate. Using voice phishing (also called vishing) and message scams (smishing), these operations have been developed into a scam call-center industry worth billions of dollars.
For starters, these ploys may not require much in the way of specialized or technical skills. Also, a single person (often a victim of human trafficking) can, at a time, ensnare multiple unwitting victims in various flavors of fraud.
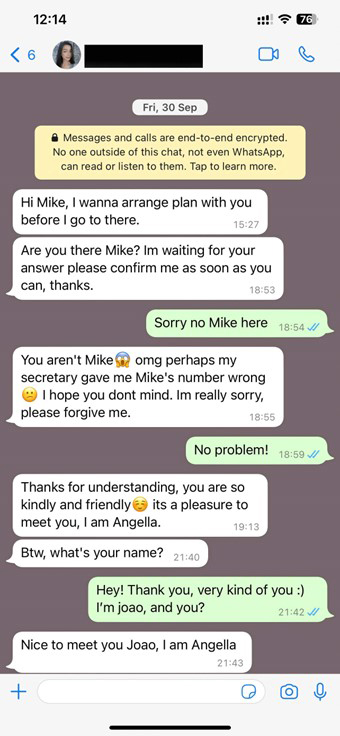
Hello? Is this thing on?
Imagine receiving a call from your bank to inform you that your account has been breached and in order to keep your money safe, you need to share your sensitive details with them. The urgency in the voice of the bank’s “employee” may indeed be enough to prompt you to share your sensitive information. The problem is, this person might not be from your bank – or they may not even exist at all. It could be just a fabricated voice, but still sound completely natural.
This isn’t at all uncommon and cautionary tales from recent years abound. Back in 2019, a CEO was scammed out of almost US$250,000 by a convincing voice deepfake of their parent company’s chief. Similarly, a finance worker was tricked via a deepfake video call in 2024, costing their firm US$25 million.
AI, the enabler
With modern AI voice cloning and translation capabilities, vishing and smishing have become easier than ever. Indeed, ESET Global Cybersecurity Advisor Jake Moore demonstrated the ease with which anybody can create a convincing deepfake version of someone else – including someone you know well. Seeing and hearing are no longer believing.
AI is lowering the barrier of entry for new adversaries, serving as a multipronged tool to gather data, automate tedious tasks, and globalize their reach. Consequently, phishing using AI-generated voices and text will probably become more commonplace.
On this note, a recent report by Enea noted a 1,265% rise in phishing scams since the launch of ChatGPT in November 2022 and spotlighted the potential of large language models to help fuel such malicious operations.
What’s your name, what’s your number?
As evidenced by Consumer Reports research from 2022, people are becoming more privacy-conscious than before. Some 75% of the survey’s respondents were at least somewhat concerned about the privacy of their data collected online, which may include phone numbers, as they are a valuable resource for both identification and advertising.
But now that we’re well past the age of the Yellow Pages, how does this connection between phone numbers and advertising work?
Consider this illustrative example: a baseball fan placed tickets in a dedicated app’s checkout but didn’t complete the purchase. And yet, shortly after closing the app, he received a phone call offering a discount on the tickets. Naturally, he was baffled since he didn’t remember providing his phone number to the app. How did it get his number, then?
The answer is – via tracking. Some trackers can collect specific information from a webpage, so after you’ve filled in their phone number in a form, a tracker could detect and store it to create what is often called personalized content and experience. There is an entire business model known as “data brokering”, and the bad news is that it doesn’t take a breach for the data to become public.
Tracking, data brokers, and leaks
Data brokers vacuum up your personal information from publicly available sources (government licenses/registrations), commercial sources (business partners like credit card providers or stores) as well as by tracking your online activities (activities on social media, ad clicks, etc.), before selling your information to others.
Still, the question on your lips may be: how can scammers obtain other people’s phone numbers?
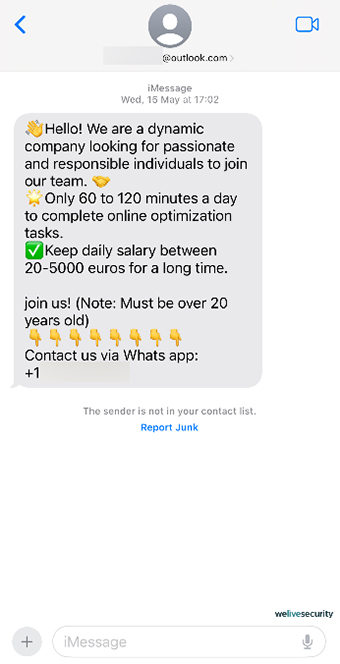
Naturally, the more companies, sites, and apps you share your personal information with, the more detailed your personal “marketing profile” is. This also increases your exposure to data leaks, since data brokers themselves can experience security incidents. A data broker could also sell your information to others, possibly including bad actors.
But data brokers, or breaches affecting them, aren’t the only source of phone numbers for scammers. Here are some other ways in which criminals can get ahold of your phone number:
- Public sources: Social media sites or online job markets might show your phone number as a means to make a connection. In case your privacy settings are not dialed in correctly or you are not aware of the consequences of revealing your phone number in your social media profile, your number might be available to anyone, even an AI web scraper.
- Stolen accounts: Various online services require your phone number, be it to confirm your identity, to place an order, or to serve as an authentication factor. When your accounts get brute-forced due to weak passwords or one of your online providers suffers a data breach your number could easily leak as well.
- Autodialers: Autodialers call random numbers, and as soon as you answer the call, you may be targeted by a scam. Sometimes these autodialers call just to confirm that the number is in use so that it can be added to a list of targets.
- Mail: Check any of your recent deliveries – these usually have your address visible on the letter/box, but in some cases, they can also have your email or phone number printed on them. What if someone stole one of your deliveries or rummaged through your recycling pile? Considering that data leaks usually contain the same information, this can be very dangerous and grounds for further exploitation.
As an example of a wide-scale breach affecting phone numbers, AT&T recently revealed that millions of customers’ call and text message records from mid-to-late 2022 were exposed in a massive data leak. Nearly all of the company’s customers and people using the cell network have had their numbers, call durations, and number of call interactions exposed. While call and text contents are allegedly not among the breached data, customer names and numbers can still be easily linked, as reported by CNN.
Reportedly, the blame can be put on a third-party cloud platform, which a malicious actor had accessed. Coincidentally, the same platform has had several cases of massive leaks linked to it in recent years.
How to protect your phone number
So, how can you protect yourself and your number? Here are a few tips:
- Be aware of phishing. Never answer unsolicited messages/calls from foreign numbers, don’t click on random links in your emails/messages, and remember to keep cool and think before you react to a seemingly urgent situation, because that’s how they get you.
- Ask your service provider about their SIM security measures. They might have an option for card locks to protect against SIM swapping, for example, or additional account security layers to prevent scams like call forwarding.
- Protect your accounts with two-factor authentication, ideally using dedicated security keys, apps, or biometrics instead of SMS-based verification. The latter can be intercepted by bad actors with relative ease. Do the same for service provider accounts as well.
- Think twice before providing your phone number to a website. While having it as an additional recovery option for your various apps might be useful, other methods like secondary emails/authenticators could offer a more secure alternative.
- For online purchases, consider using a pre-paid SIM card or a VoIP service instead of your regular phone number.
- Use a mobile security solution with call filtering, as well as make sure that third-party cookies in your web browser are blocked, and explore other privacy-enhancing tools and technologies.
In a world that increasingly relies on online record keeping, there is a low chance that your number won’t be preserved by a third party somewhere. And as the AT&T incident suggests, relying on your own carrier’s security is also rather problematic. This doesn’t mean that you should remain in a state of constant paranoia, though.
On the other hand, it highlights the importance of committing to proper cyber hygiene and being aware of your data online. Vigilance is also still key, especially when considering the implications of this new, AI-powered (under)world.
by Mark Szabo, on eof our friends at ESET. The ESET blog can be found here.
- iPing
In today's interconnected digital landscape, businesses face an ever-growing array of cybersecurity threats. The recent global outage of Crowdstrike, a leading cybersecurity provider, on July 19th, 2024, serves as a stark reminder of the critical role that security software plays in maintaining business continuity. This incident, which affected numerous industries including airlines, financial institutions, and healthcare providers, underscores the importance of robust security measures and the potential consequences of over-reliance on a single vendor. Let's delve deeper into the implications of this event and explore why comprehensive security strategies are vital for every organisation.
Understanding the Crowdstrike Outage
The Catalyst: A Faulty Update
The Crowdstrike outage was triggered by a faulty software update that led to widespread issues with Microsoft systems. This seemingly routine maintenance task cascaded into a global disruption, affecting countless businesses relying on Crowdstrike's security solutions.
The Ripple Effect
The impact of the outage was far-reaching and severe:
-
Aviation Industry: Major airlines were forced to ground flights due to compromised security systems, leading to travel chaos and significant financial losses. At the time of writing the number of cancelled flights stands at over 3,300!
-
Financial Sector: Banks and financial institutions experienced disruptions in transaction processing, affecting everything from ATM withdrawals to stock market trades.
-
Healthcare: Hospitals and clinics faced challenges in accessing patient records and securing sensitive medical data.
-
Retail: E-commerce platforms and point-of-sale systems were compromised, resulting in lost sales and potential data breaches.
-
Government Services: Some government agencies experienced interruptions in their operations, potentially impacting public services.
Key Lessons
This incident illuminates several critical lessons for businesses:
-
Diversification is Key: Over-reliance on a single security vendor can leave an organisation vulnerable. A multi-vendor approach can provide redundancy and reduce risk.
-
Proactive Measures are Essential: Regular system audits, update testing, and having contingency plans in place can mitigate the impact of such incidents.
-
Communication is Crucial: Many businesses were caught off-guard by the sudden outage. Improved communication channels between vendors and clients could have allowed for better preparation.
The Indispensable Role of Security Software
In light of the Crowdstrike incident, it's crucial to understand why security software is indispensable for modern businesses.
Types of Security Software
Different types of security software serve specific purposes in protecting an organisation's digital assets:
|
Software Type |
Function |
Examples |
|
Endpoint Protection |
Safeguards individual devices from malware and other threats |
ESET, Symantec, Kaspersky |
|
Firewalls |
Monitors and controls network traffic based on predetermined security rules |
Cisco ASA, Sonicwall, Fortinet |
|
Intrusion Detection Systems (IDS) |
Identifies potential security breaches, including both attacks from outside and inside the network |
Snort, Suricata, OSSEC |
|
Antivirus Software |
Detects, prevents, and removes malicious software |
ESET, Bitdefender, Avast |
|
Protects against phishing, spam, and malware delivered via email |
Mimecast, TopSec, Barracuda |
Benefits of Robust Security Software
-
Protection Against Evolving Threats: As cyber threats become more sophisticated, security software evolves to counter new attack vectors.
-
Data Breach Prevention: Effective security measures can significantly reduce the risk of costly and reputation-damaging data breaches.
-
Regulatory Compliance: Many industries are subject to strict data protection regulations. Security software helps ensure compliance with these standards.
-
Business Continuity: By preventing successful attacks, security software helps maintain uninterrupted business operations.
-
Customer Trust: Demonstrating a commitment to security can enhance customer confidence and loyalty.
Selecting the Right Security Solution
When choosing security software, businesses should consider:
-
Scalability: The solution should be able to grow with the business.
-
Integration: It should work seamlessly with existing systems and software.
-
Industry-Specific Features: Different sectors may require specialised security features.
-
User-Friendliness: The software should be easy for staff to use and for IT teams to manage.
-
Support and Updates: Regular updates and responsive customer support are crucial.
-
Cost-Effectiveness: While security is essential, it's important to find a solution that fits within the budget.
Beyond Software: A Holistic Approach to Security
While security software is crucial, a comprehensive security strategy extends beyond relying solely on software solutions.
The Importance of Regular Backups
Regular, secure backups are a critical component of any business continuity plan:
-
Data Recovery: In the event of system failures or successful cyberattacks, backups allow for quick data recovery.
-
Ransomware Mitigation: With secure backups, businesses can avoid paying ransoms to recover their data.
-
Compliance: Many regulatory frameworks require businesses to maintain backups of critical data.
Employee Training: The Human Firewall
Human error remains one of the biggest security vulnerabilities for organisations. Comprehensive employee training is essential:
-
Phishing Awareness: Teach employees to identify and report suspicious emails and links.
-
Password Hygiene: Encourage the use of strong, unique passwords and multi-factor authentication.
-
Data Handling: Train staff on proper procedures for handling sensitive information.
-
Social Engineering: Educate employees about various social engineering tactics used by cybercriminals.
Implementing a Multi-Layered Security Approach
A robust security strategy incorporates multiple layers of protection:
-
Network Segmentation: Divide the network into subnetworks to limit the spread of potential breaches.
-
Regular Patching and Updates: Keep all systems and software up-to-date to address known vulnerabilities.
-
Access Control: Implement the principle of least privilege, giving users only the access they need.
-
Encryption: Use strong encryption for sensitive data, both in transit and at rest.
-
Incident Response Plan: Develop and regularly test a plan for responding to security incidents.
-
Third-Party Risk Management: Assess and monitor the security practices of vendors and partners.
Conclusion: Securing the Future of Your Business
The Crowdstrike outage of July 2024 serves as a wake-up call for businesses worldwide. It highlights the critical importance of robust security measures and the potential risks of over-reliance on a single security provider. As cyber threats continue to evolve in sophistication and frequency, organisations must adopt a proactive and comprehensive approach to cybersecurity.
Investing in reliable security software is a crucial first step, but it's only part of the equation. Businesses must also focus on employee training, regular system updates, data backups, and developing incident response plans. By implementing a multi-layered security strategy, organisations can better protect their operations, data, and reputation in an increasingly complex digital landscape.
The time to act is now. Evaluate your current security posture, identify potential vulnerabilities, and take steps to strengthen your defences. Remember, in the world of cybersecurity, prevention is always better than cure. By prioritising security today, you're not just protecting your current assets – you're securing the future of your business.
iPing can provide your business with some excellent security and backup solutions to help take away the worries of incidents like this negatively impacting your day to day performance. Contact us today on 01 524 1350 to learn more about what we can do for you.
- iPing
Introduction
In the ever-evolving landscape of cybersecurity, the threat of phishing and spoofing attacks has become increasingly prevalent. As businesses continue to rely on email as a primary mode of communication, it's crucial to prioritize the security of these digital channels. One such area that demands attention is the security of Office 365 email, a platform that has risen in popularity and, consequently, become a prime target for malicious actors.
Starting in 2024, both Google and Yahoo now require bulk email senders to implement DKIM and DMARC on their email systems. There are limited penalties initially, but the severity will increase over time.
To combat these challenges, two key email authentication protocols have emerged as essential tools in the arsenal of modern cybersecurity: DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting & Conformance). These protocols work in tandem to provide a robust defense against phishing and spoofing attempts, ensuring the integrity of your business email communications.
What are DKIM and DMARC?
DKIM (DomainKeys Identified Mail)
DKIM is an email authentication protocol that adds a digital signature to outgoing emails. This signature allows recipient email servers to verify the authenticity of the sender's domain, ensuring that the email has not been tampered with or spoofed.
The DKIM authentication process works as follows:
- The email sender's email server generates a private cryptographic key and a public key.
- The private key is used to sign the email's content and header information, creating a digital signature.
- The public key is then published in the sender's Domain Name System (DNS) records, allowing recipient email servers to access and verify the signature.
- When the recipient email server receives the message, it retrieves the public key from the sender's DNS records and uses it to validate the digital signature. If the signature is valid, the email is deemed authentic.
DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC builds upon the foundations of two other email authentication protocols: Sender Policy Framework (SPF) and DKIM. While SPF and DKIM provide the means to authenticate the sender's domain, DMARC takes it a step further by specifying how recipient email servers should handle messages that fail authentication.
DMARC accomplishes this by:
- Telling recipient email servers what to do with emails that fail SPF or DKIM authentication (e.g., reject, quarantine, or simply report the failure).
- Providing a mechanism for the sender to receive detailed reports about the authentication status of their emails, allowing them to monitor and troubleshoot any issues.
By implementing DMARC, businesses can take a proactive approach to protecting their domain from being used in phishing and spoofing attacks.
Why DKIM and DMARC Matter in 2024
In an era where cyber threats continue to grow, email remains one of the most vulnerable attack vectors for businesses. Phishing scams, increasingly sophisticated spoofing attempts, and fraudulent emails disguised as legitimate business communications pose a significant risk to organizations of all sizes. This is where DKIM and DMARC step in as vital defenses.
- Protection Against Spoofing and Phishing: The primary function of both DKIM and DMARC is to prevent attackers from impersonating your business domain. DKIM adds a digital signature to your outgoing emails, allowing recipient servers to verify that the email truly originated from your company. DMARC then dictates how to deal with emails that fail authentication – they can be quarantined or outright rejected. This combination significantly reduces the success rate of spoofing and phishing attempts.
- Improved Email Deliverability: Emails lacking proper authentication are much more likely to be caught in spam filters or even blocked entirely by recipient mail servers. Both DKIM and DMARC act as signals of trustworthiness, establishing you as a legitimate sender. This leads to better inbox placement and a higher chance of your important emails reaching their intended targets.
- Enhanced Brand Reputation: With DKIM and DMARC in place, you substantially lower the risk of your clients or customers falling victim to fraudulent emails sent in your company's name. This protects your brand's reputation and fosters trust, as your recipients are more confident that emails sent from your domain are genuine.
- Compliance and Increased Security Posture: Certain industries and regions may have regulatory requirements around email security. Implementing DKIM and DMARC often helps meet these compliance standards. Moreover, these protocols contribute to a more robust overall cybersecurity posture, minimizing the risk of email-based attacks.
The Urgency of 2024
While these benefits have always been important, the year 2024 brings a sense of urgency. Major email providers like Google and Yahoo have set deadlines for stricter DMARC enforcement policies for bulk email senders. To ensure seamless delivery and avoid disruptions, businesses need to have their DKIM and DMARC configuration in place well ahead of time.
In Summary
DKIM and DMARC are not merely technical niceties – they're safeguards for your business communications. In 2024, their role in protecting your company reputation, preventing financial losses due to fraud, and ensuring your emails reliably reach their destination is more critical than ever.
Conclusion
In the ever-evolving landscape of cybersecurity, the security of your business email communications must be a top priority. DKIM and DMARC have emerged as essential tools in the fight against phishing and spoofing attacks, particularly for organizations relying on Office 365 as their email platform.
By implementing these protocols, you can protect your business from email-based threats, improve email deliverability, and safeguard your brand reputation. As we move forward into 2024 and beyond, the adoption of DKIM and DMARC will continue to be a critical step in ensuring the security and reliability of your email communications.
Don't wait to secure your business email. Take the necessary steps to implement DKIM and DMARC today, and ensure that your organization is better equipped to navigate the challenges of the digital age.
iPing provides managed services and IT services. We can help provide you with an overview of your current setup, and what email protections you have in place. So if you need some help with implementing DKIM or DMARC on your system then please contact us or give us a call on 01-5241350.
- iPing
Cloud computing has revolutionized businesses of all sizes by providing on-demand access to computing resources, storage, applications and services over the internet. As per Gartner, the worldwide public cloud services market is projected to grow 17% in 2022 to total $494.7 billion. With over 90% of enterprises already adopting cloud solutions and migration accelerating, it is clear that the cloud empowers efficiency, flexibility and competitive advantage like never before.
The Power of Cloud Computing for Efficiency
Migrating to the cloud eliminates the upfront infrastructure expenses associated with traditional on-premises IT deployments. Businesses no longer need to invest heavily in purchasing, managing and maintaining their own hardware and data centers. The pay-as-you-go subscription model allows usage-based payment for exactly the resources utilized. This optimization reduces costs by 25% to 50% compared to on-premises solutions.
With cloud computing, businesses tap into virtually unlimited on-demand compute, storage and services. This ready availability of automated resources dramatically improves IT responsiveness to business needs. Companies can quickly rollout applications and services without prolonged hardware procurement delays. IT staff spend less time on infrastructure management and more time focusing on innovative projects that create value.
According to LogicMonitor, 83% of enterprises reported improved IT staff efficiency after cloud migration. With limited resources needed to maintain and update systems, the cloud frees up time for strategic initiatives. The self-service provisioning also allows business units to rapidly acquire resources without IT bottlenecks.
Unlocking Flexibility with Cloud Computing
The on-demand scalability of cloud computing allows adjustment of capacity to seamlessly align with fluctuating business needs. Usage can be scaled elastically to accommodate demand surges like a viral marketing campaign or seasonal order spike. Additional computing capacity gets rapidly provisioned to handle the increased traffic and ensure consistent application performance. Once demand stabilizes, capacity can be scaled back down to control costs.
The flexibility extends to remote access from anywhere at anytime. As long as there is internet connectivity, cloud-based apps and data can be securely accessed with any device globally. This enables a distributed workforce to collaborate productively from diverse locations. Cloud computing overcomes geographical barriers to business growth.
While public clouds meet most workload requirements, businesses with legacy systems or stringent compliance needs depend on private clouds. Hybrid cloud solutions integrate both public and private environments with workload mobility across platforms. This balances agility, control, compliance and economics optimally based on application needs.
Enhancing Collaboration and Productivity
Cloud-based productivity suites and content workflow apps connect distributed teams to work cohesively. These facilitate real-time messaging, video conferences, collaborative document editing and seamless file sharing. Desktops and networks need no longer constrain workforce mobility or productivity.
Built on cloud platforms, Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM) solutions break departmental information silos. Sales, finance, inventory and support can securely share integrated customer data on the cloud for consistent omni-channel experiences. Supply chain coordination and inventory optimization improves with cross-location transparency.
As per Cisco, hybrid work leads to additional productivity gain of ~5 hours per employee per week. Collaboration tools like Microsoft Teams, Google Workspace, Dropbox and Slack enabled the widespread enterprise adoption of hybrid work models. With the cloud erasing geographical divides, global enterprises gain expanded access to talent and 24/7 productivity leveraging timezone differences.
Securing Data and Protecting Businesses
As digital transformation accelerates, security concerns around cloud adoption are being addressed by robust data safeguards. Leading cloud providers employ advanced threat protection, predictive analytics, anomaly detection, encryption and malware prevention capabilities. Stringent physical datacenter security protocols restrict unauthorized access further.
With in-built redundancy across fault domains and availability zones, enterprise cloud platforms provide resilience against outages. Regular automated data backups, multiple replicas across regions and mirroring to disaster recovery sites protect against data loss. Cloud systems sustained uptime exceeds 99.99% even during recent disruptions like the Covid-19 pandemic.
The scale of public cloud providers ensures dedicated security and compliance specialists stay continually up-to-date with the newest attack vectors and regulations. This expertise would be challenging for businesses to replicate in-house cost-effectively. Leading platforms like Microsoft Azure, AWS and Google Cloud provide industry-compliant solutions to address regional and vertical regulatory mandates around data governance, security and privacy.
Achieving Business Agility and Competitive Advantage
With speed to market critical for growth, the business agility enabled by cloud computing empowers competitive differentiation. Enterprises can launch innovative ideas faster by leveraging cloud provider ecosystems for prebuilt solutions spanning IoT, analytics, blockchain and machine learning. Instead of prolonged hardware procurement and solution development cycles, preconfigured cloud templates help quickly turn ideas into market-ready offerings.
The elastic infrastructure facilitates rapid scaling to gain market share and respond to emerging segments. By eliminating capacity planning guessing games, the cloud allows focusing resources on developing must-have solutions over predicting server demand. It fosters a fail-fast product iteration culture geared towards continuous customer value enhancement.
Cloud adoption forms the flexible digital core to future-proof business models. It enables establishing platform business models like Netflix, Uber and Airbnb which have disrupted entire industries. With the cloud equalizing access to enterprise-grade technology, it levels the playing field for small businesses to cost-effectively compete and thrive.
Conclusion
Cloud computing has cemented its position as the platform for transformative business growth with over 90% enterprises already on the cloud journey. Its undeniable benefits in terms of efficiency, flexibility, collaboration and security explain the accelerating adoption across businesses of all sizes. As competitive differentiation gets increasingly tied to technology-fueled innovation, the cloud provides the strategic springboard for operational excellence.
The unlimited on-demand compute access empowers unprecedented economies of scale while eliminating hardware bottlenecks and IT maintenance burdens. This unleashes business productivity to greater heights. Now cloud-powered, future-ready and resilient, enterprises stand primed to seize market opportunities faster. So get ready to accelerate your cloud journey and unlock your organization’s true potential.
- iPing
Finding reliable and affordable tech support in Dublin can be a real challenge for businesses and individuals. With the growing dependence on technology across all sectors, having access to quality IT services has become crucial. This article will serve as an in-depth guide on how to find the top tech support companies in Dublin to meet your specific needs.
The Importance of Tech Support in Dublin
Technology now plays a pivotal role in how businesses operate and individuals manage their daily lives. From cloud computing to e-commerce, most activities rely heavily on technology functioning smoothly. Tech support provides that critical service to troubleshoot IT issues quickly and efficiently. Benefits include:
- Increased productivity and optimization of technological systems
- Reduced downtime that disrupts operations
- Enhanced cybersecurity measures
- Cost-savings over the long run
However, with an abundance of options in Dublin, selecting the right tech support can be overwhelming. By understanding the services offered and top providers in the city, you can make an informed decision suitable to your requirements and budget.
Overview of Tech Support Services Offered in Dublin
A range of tech support services cater to both small and large organizations in Dublin. These can broadly be categorized as:
On-Site Support
- Technicians visit your office or location to troubleshoot IT issues
- Quick response time for mission-critical problems
- Hands-on assessment and fixing of problems
- Ideal for complex technological infrastructures
Remote Monitoring and Support
- Access to technicians over phone, email or screen sharing apps
- Regular remote IT infrastructure monitoring
- Quick solutions for software, network issues
- Cost-saving service efficient for small businesses
Managed IT Services
- Packaged plans for all IT support and management needs
- Combination of on-site visits, remote support and project work
- Monthly/annual contracts with scheduled hours
- Suited for growing companies looking to outsource IT
Cloud-Based Support
- Hosting data and apps on remote cloud servers
- Tech troubleshooting provided by cloud services provider
- Reduced infrastructure costs and hardware needs
- Scalable and flexible capacity
Choosing the Right Tech Support Company
With tech advancements and new methodologies frequently arising, reviewing the following pointers will assist in determining the best tech support firm for your specific organizational goals:
| Criteria | Evaluation Questions |
|---|---|
| Type of Technical Support | Will onsite assistance be required or remote troubleshooting sufficient? Any need for multilingual support? |
| Industry Experience | Does the provider possess experience handling IT systems within your sector? |
| Business Size Suitability | Are the available plans and services a good fit for your employee count and office scale? |
| Cost Structure | What is the pricing model - project-based, monthly/annual contracts? Within defined budget? |
| Response Time | Is guaranteed response time for tech issues outlined clearly? |
| Security Protocols | Does the company follow stringent cybersecurity processes and protocols? |
| Reviews & Testimonials | Can the provider furnish reliable client reviews and feedback when requested? |
Why Choose iPing?
iPing is a company that specializes in providing professional managed IT services to businesses in Dublin and the surrounding areas. Their services include monitoring, managing, and supporting their clients' IT infrastructure, allowing businesses to focus on their core activities.
iPing offers a range of services tailored to the evolving needs of technology-driven businesses. These services include:
Outsourced IT Department: Providing solutions for managing in-house IT departments, which can be costly and resource-intensive.
Cyber Security: Ensuring the security of business data in the digital landscape.
Break-Fix Services: Offering reliable solutions for unexpected IT issues to keep businesses running smoothly.
IT Audits: Conducting regular IT audits in the rapidly evolving technology landscape.
IT Strategic Planning: Assisting in defining IT strategies crucial for business success and growth.
Hardware & Software Sales: Providing a comprehensive range of high-quality IT hardware solutions.
Key Benefits of Tech Support Services in Dublin
Developing a partnership with a trusted tech support company in Dublin drives quantifiable long term value for your business through:
Enhanced Productivity
Smoothly operating technology with limited downtime translates to higher employee productivity and optimized workflows.
Reduced Business Disruptions
Expert IT assistance helps mitigate technical glitches that can hamper core operations and affect customer service.
Robust Cybersecurity
Advanced monitoring, data encryption and antivirus software provide vital protection against phishing attacks, hacking attempts and malware.
Cost Savings
Proactive maintenance and IT troubleshooting reduces spend from expensive equipment upgrades/replacements due to outdated infrastructure.
Scalability for Future Growth
As your organization grows, a reliable tech provider can seamlessly scale their services to match your operational requirements.
Tips for Finding Top Tech Support in Dublin
Use these practical tips to aid your search for the premier enterprise grade technical support in Dublin:
- Ask for Referrals: Consult your business circle and other owners for tech provider recommendations based on word-of-mouth positivity.
- Check Online Reviews: Reliable customer testimonials and favourable online ratings indicate reputable services.
- Compare Service Offerings: Evaluate the diversity of support provided – remote staff training, cloud assistance, hardware consultations etc.
- Meeting/Quote: Have an introductory call/meeting and get written quotes from a few shortlisted companies before deciding.
- Visit Industry Events: Attend relevant IT-focused exhibits and conferences to engage directly with tech support representatives.
- Leverage Directories: Consult recognized annual lists ranking the top tech support firms in Dublin and Ireland.
Conclusion - Prioritize Tech Support for Long Term Success
As discussed through the article, identifying and investing in robust IT infrastructure support tailor-made to your entity’s needs is essential for gaining a competitive edge. With data and insight provided on Dublin’s finest tech support companies around service categories, suitability factors and proven advantages, the process is simplified. Don’t delay - get in touch today for a consultation on leveraging innovative technological solutions pertinent for your business growth and continuity.
- iPing
In a rapidly evolving digital landscape, the need for robust and reliable IT infrastructure is imperative. Managed IT services have emerged as a beacon of relief for businesses striving to stay afloat amidst the technological whirlwind. By outsourcing IT operations to specialised vendors, companies not only enhance operational efficiency but unlock new avenues for growth and innovation. The keyword, "Top Managed IT Services to Propel Your Business" encapsulates a realm of IT solutions meticulously curated to fuel your business's engine towards an era of digital dominance.
Introduction to Managed IT Services
Managed IT Services signify a paradigm shift from the traditional break-fix model to a more proactive and predictable model. The essence lies in the proactive management of IT assets to prevent issues before they escalate into major problems. This model is not only cost-effective but ensures a smoother operational flow and better alignment with business objectives.
In earlier times, businesses would react to IT issues as they arose, often leading to unexpected downtime and financial losses. The managed IT services model, on the other hand, emphasises continuous monitoring and maintenance to prevent such issues from occurring in the first place.
The Rise of Managed IT Services
Tracing back the lineage of managed IT services unveils a compelling narrative of technological evolution. Over the decades, as businesses burgeoned in complexity, so did their IT needs. The market responded with a spectrum of managed IT services, each designed to cater to distinct facets of IT operations.
The adoption of managed IT services has skyrocketed, especially in the last decade, as organisations realised the immense value they bring to the table. Not only do they help in streamlining operations, but they also help businesses stay compliant, secure, and ahead in the technology curve.
Top Managed IT Services to Propel Your Business
The marketplace is replete with a myriad of IT services, yet a select few stand tall in propelling businesses to the zenith of operational excellence. Let's delve deeper into these pivotal services:
IT Infrastructure Management
A robust IT infrastructure is the backbone of a thriving business in the digital age. It entails managing the core hardware, software, and network resources efficiently. Engaging with managed IT services for infrastructure management ensures a resilient and optimised IT environment. An optimised IT infrastructure can significantly reduce operational hiccups and ensure that the business operations run smoothly.
Cybersecurity Services
In an era where data breaches are commonplace, safeguarding business assets is paramount. Cybersecurity services offer a fortified shield against a myriad of cyber threats, ensuring business continuity and trust. By implementing advanced security measures, monitoring for threats in real time, and ensuring compliance with various regulatory standards, cybersecurity services play a crucial role in safeguarding business assets.
Cloud Services
Cloud services offer a pathway to enhanced scalability, flexibility, and cost-effectiveness. It’s a catalyst for fostering innovation and agility in business operations. The cloud empowers businesses with the ability to access data and applications from anywhere, anytime, thus enhancing productivity and collaboration.
Communication and Collaboration Services
Effective communication is the linchpin of successful project execution. These services optimise communication channels and foster a collaborative environment within the organisation. Modern communication and collaboration tools such as video conferencing, instant messaging, and project management software have revolutionised the way teams work together.
Data Analytics
Transforming raw data into actionable insights is a forte of data analytics services. They empower businesses to make data-driven decisions, propelling them towards a competitive edge. By harnessing the power of data analytics, businesses can uncover trends, monitor performance, and identify areas for improvement.
Support and Maintenance
Continuous support and diligent maintenance are vital for ensuring operational continuity. These services provide a safety net for businesses to operate seamlessly. A dedicated support team ensures that any issues are swiftly resolved, minimising downtime and ensuring a smooth operational flow.
Transitioning to a Managed IT Service Provider
Transitioning to a managed IT service provider necessitates a thorough understanding of your current IT landscape, identifying the areas that require external support, and choosing a provider that aligns with your business goals. The right managed IT service provider will not only address your immediate concerns but will be a partner in your long-term growth.
Overcoming Common Challenges
Transitioning to managed IT services can come with its own set of challenges. Concerns regarding data security, cost, and control are common. However, with the right provider, these challenges can be mitigated to a great extent. It's about building a partnership that's rooted in trust, transparency, and mutual growth.
Your Path Towards Leveraging Managed IT Services
Embarking on a journey towards leveraging top managed IT services can be a game-changer for your business. It's an investment in fostering a resilient, efficient, and innovative operational landscape that can propel your business towards unprecedented heights. The road ahead is filled with opportunities for growth, efficiency, and innovation. Seize them with the right managed IT service partner by your side.
iPing are an Irish based Outsource IT support for small and medium sized businesses. We help businesses grow by ensuring their IT systems are operating fully at all times and if there are IT issues, we are on it straight away.
We provide back up, technical updates, monitoring, IT strategic advice, protection, but most importantly we keep your IT systems operating so you can focus on your business.










